What is the MHA Nation Tax department doing to protect your information and its Data collected?
- Is the tax-mhanation.com website secured?
Yes, it is secured. We have added an SSL certificate to the site for an added layer of security to ensure our customers data is encrypted.
- What is an SSL Certificate?
SSL Certificates are small data files that digitally bind a cryptographic key to an organization’s details. When installed on a web server, it activates the padlock and the https protocol and allows secure connections from a web server to a browser. Typically, SSL is used to secure credit card transactions, data transfer and logins, and more recently is becoming the norm when securing browsing of social media sites.
Here is a link to a video to help explain on what an SSL Certificate is.
https://youtu.be/dsuVPxuU_hc
- How can I tell if a website is safe?
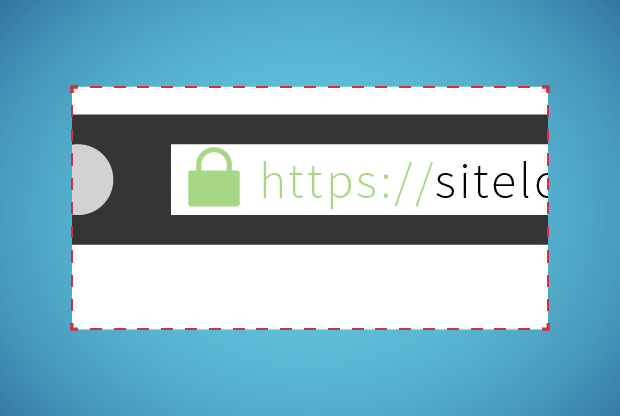
- Look fir the “S” in the HTTPS, If HTTPS sounds familiar, it should. Many URLs begin with “https” instead of just “http” to indicate that they are encrypted. This security is provided by an SSL certificate, which protects sensitive information entered into that site as it travels from the site to a server. Without an SSL certificate, that information is exposed and easily accessible by cybercriminals. It’s important to note that HTTPS isn’t the only thing a website can – or should do – to protect its visitors, but it’s a good sign that the website owner cares about your safety. Whether you’re logging in, making a payment, or just entering your email address, check that the URL starts with “https.”
- Check for a website privacy policy

A website’s privacy policy should clearly communicate how your data is collected, used, and protected by the website.Nearly all websites will have one, as they are required by data privacy laws in countries like Australia and Canada, and even stricter rules have been introduced in the EU. A privacy policy indicates that the website owner cares about complying with these laws and ensuring that their website is safe. Be sure to look for one, and read it over, before giving your information to a website.
- Find their contact information.
If finding a website’s contact information makes that site seem more trustworthy to you, you’re not alone. A survey of website visitors found that 44 percent of respondents will leave a website that lacks a phone number or other contact information. Ideally, a safe website will clearly display an email address, a phone number, a physical address if they have one, return policy if applicable, and social media accounts. These won’t necessarily provide protection, but they indicate that there’s likely someone you can reach out to if you need assistance.
- Verify their trust seal

If you see an icon with the words “Secure” or “Verified,” it’s likely a trust seal. A trust seal indicates that the website works with a security partner. These seals are often an indicator that a site has HTTPS security, but they can also indicate other safety features, like the date since the site’s last malware scan.
Although 79 percent of online shoppers expect to see a trust seal, the presence of the seal isn’t enough. It’s also important to verify that the badge is legitimate. Fortunately, it’s easy to do – simply click the badge and see if it takes you to a verification page. This confirms that the site is working with that particular security firm. It doesn’t hurt to do your own research on the company supplying the badge, too!
If a trust seal is legitimate, clicking on it will take you to a page that verifies the authenticity of that seal. As an example, SiteLock’s verification page looks like this.



- Know the signs of website malware

Even if a website has an SSL certificate, a privacy policy, contact information, and a trust badge, it may still not be safe if it is infected with malware. But how do you know if a website is infected with malware? Look for the signs of these common attacks:
- Defacements. This attack is easily spotted: cybercriminals replace a sites content with their name, logo, and/or ideological imagery.
- Suspicious pop ups. Be cautious of pop ups that make outlandish claims – they are likely trying to entice you to click and accidentally download malware.
- Malvertising. Some malicious ads are easy to catch. They typically appear unprofessional, contain spelling/grammar errors, promote “miracle” cures or celebrity scandals, or feature products that don’t match your browsing history. It’s important to note that legitimate ads can also be injected with malware, so exercise caution when clicking.
- Phishing kits. Phishing kits are websites that imitate commonly visited sites, like banking websites, to trick users into handing over sensitive information. They may appear legitimate but spelling and grammar errors will give them away.
Malicious redirects. If you type in a URL and are redirected to another site – especially one that looks suspicious – you have been affected by a malicious redirect. They are often used in conjunction with phishing kits.
- SEO spam. The appearance of unusual links on a site, often in the comments section, is a sure sign of SEO spam.
- Does the MHA Nation Tax department have anti-virus software on their devices?
Yes, we are using the latest version of Bitdefender Endpoint Security.
- What is the Customer Tax Access Portal?
The Customer Tax Access Portal is method for our customers to pay for their taxes and fees online.
- How is my information being protected once I have created an online account and start entering my information in the Customer Tax Access Portal?
Please follow link to read Encryption in the Microsoft Cloud.
- Secure Identity
Microsoft Dynamics 365 relies on Azure Active Directory (AAD) to provide authentication for users, helping to protect Dynamics 365 from unauthorized access. It simplifies the management of users and groups and enables you to assign and revoke privileges.
Dynamics 365 uses the same identity platform as Microsoft Office 365, so a user of both services has the same username and password. Customers can federate an on-premises AAD or other directory stores to enable using corporate credentials to authenticate.
- Secure apps and data
Data protection
Dynamics 365 uses encryption to protect your data. Connections established between customers and Microsoft datacenters are encrypted, and public endpoints are secured using industry-standard Transport Layer Security (TLS). TLS effectively establishes a security-enhanced browser-to-server connection to help ensure data confidentiality and integrity between devices and datacenters.
We also provision your organization with its own logically isolated data repository to maximize the security and integrity of your data. And, when systems become outdated or are no longer operational, Microsoft operations personnel follow rigorous data-handling procedures and hardware disposal processes.
- Secure Infrastructure
Security built in
Microsoft Dynamics 365 is hosted in Microsoft datacenters and uses security measures and mechanisms to protect data. Microsoft blocks unauthorized traffic to and within datacenters, using a variety of technologies such as distributed denial-of-service (DDoS) attack prevention. We constantly maintain, enhance, and verify the infrastructure, and employ regular penetration testing to continually validate the performance of security controls and processes.
Dynamics 365 is designed on the principles of the Security Development Lifecycle, a mandatory Microsoft process that embeds security requirements into every phase of development. Dynamics 365 also follows the rigorous standards set by Microsoft Operational Security Assurance to help protect customer data.
Role-based security
Microsoft Dynamics 365 uses role-based security. Role-based security is aligned with the structure of the business. You are assigned to security roles based on your responsibilities in the organization and your participation in business processes. Access is granted to these security roles rather than to individuals. The administrator grants access based on the duties individuals perform in their roles, not to the program elements used by those individuals to fulfill their roles.
The security model of Microsoft Dynamics 365
Threat management
Dynamics 365 leverages the Microsoft Cyber Defense Operations Center (CDOC), which brings together security response experts from across the company to help protect, detect and respond 24x7 to security threats against our infrastructure and services in real-time. Informed by trillions of data points across an extensive network of sensors, devices, authentication events and communications, the CDOC teams employ automated software, machine learning, and behavioral analysis and forensic techniques to protect all endpoints, better detect attacks, and accelerate our response.
Learn more about cyber defense best practices
Physical security
Microsoft Dynamics 365 is deployed in Microsoft datacenters, which are protected by defense-in-depth security that includes perimeter fencing, video cameras, security personnel, secure entrances, and real-time communications networks. The defense-in-depth security continues through every area of the facility and to each physical server unit. The Microsoft Cloud Infrastructure and Operations Group delivers the core infrastructure and foundational technologies for Dynamics 365. Our datacenters comply with industry standards for physical security and reliability and are managed, monitored, and administered by Microsoft operations personnel.



